The antivirus software company Doctor Web has issued an alert about a new form of crypto-ransomware that targets users of Linux-based operating systems. Designated as "Linux.Encoder.1" by the company, the malware largely targets Web servers, encrypting their contents and demanding a ransom of one Bitcoin (currently about $500).
Many of the systems that have been affected by the malware were infected when attackers exploited a vulnerability in the Magento CMS. A critical vulnerability patch for Magneto, which is used to power a number of e-commerce sites, was published on October 31. Doctor Web researchers currently place the number of victims in the "at least tens" range, but attacks on other vulnerable content management systems could increase the number of victims dramatically.
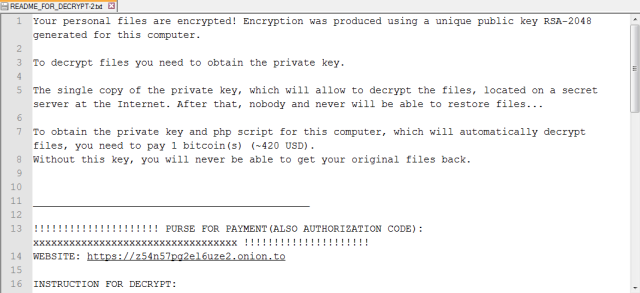
In order to run, the malware has to be executed with administrator-level privileges. Using 128-bit AES crypto, the malware encrypts the contents of all users' home directories and any files associated with websites running on the systems. It then goes through the whole directory structure of mounted volumes, encrypting a variety of file types. In each directory it encrypts, it drops a text file called README_FOR_DECRYPT.txt. This demands payment and provides a link to a Tor "hidden service" site via a Tor gateway.
The malware specifically looks for Apache and Nginx installations as well as MySQL installs in the directory structure of the targeted systems. It also seeks log directories and the location of webpage contents before ultimately going after a variety of file types—including Windows executables, program libraries and Active Server Pages (.asp) files, and SQL, Java, JavaScript, and document files. If the victim makes a payment, the malware itself will then initiate decryption of the files. The malware decrypts them in the same order that it encrypted them, deleting the encrypted versions of the files along with the ransom note text files.
Update: An automated decryption tool for victims of the Linux.Encoder.1 malware is now available for download from Bitdefender. The malware code uses a predictable method to generate its AES private encryption keys on the victim PC.
reader comments
79