How to Encrypt Directories/Partitions with eCryptfs on Debian 8 (Jessie)
eCryptfs is a POSIX-compliant enterprise-class stacked cryptographic filesystem for Linux. You can use it to encrypt partitions and also directories that don't use a partition of their own, no matter the underlying filesystem, partition type, etc. This tutorial shows how to use eCryptfs to encrypt a directory on Debian Jessie.
1 Preliminary Note
In this tutorial, I will encrypt my home directory, /home/falko/, which is located on the / partition (i.e., /home/falko/ is an ordinary directory and does not use a partition of its own).
2 Installing eCryptfs
eCryptfs can easily be installed as follows:
apt-get -y install ecryptfs-utils
3 Encrypting a directory
I will now encrypt my home directory /home/falko/. As there are already (unencrypted) files in that directory, I must take a backup of them so that I can restore them to the then encrypted /home/falko/ directory later on (otherwise these filles cannot be accessed/read while the directory is encrypted):
cp -pfr /home/falko/ /tmp/
I can now encrypt the directory /home/falko/ by mounting it with the file system type ecryptfs:
mount -t ecryptfs /home/falko /home/falko
When you do this for the first time, you will have to answer a few questions:
root@server1:/tmp# mount -t ecryptfs /home/falko /home/falko
Select key type to use for newly created files:
1) tspi
2) passphrase
Selection: <-- 2
Passphrase: <-- Enter a secure password
Select cipher:
1) aes: blocksize = 16; min keysize = 16; max keysize = 32
2) blowfish: blocksize = 8; min keysize = 16; max keysize = 56
3) des3_ede: blocksize = 8; min keysize = 24; max keysize = 24
4) twofish: blocksize = 16; min keysize = 16; max keysize = 32
5) cast6: blocksize = 16; min keysize = 16; max keysize = 32
6) cast5: blocksize = 8; min keysize = 5; max keysize = 16
Selection [aes]: <-- Press ENTER
Select key bytes:
1) 16
2) 32
3) 24
Selection [16]: <-- Press ENTER
Enable plaintext passthrough (y/n) [n]: <-- Press ENTER
Enable filename encryption (y/n) [n]: <-- Press ENTER
Attempting to mount with the following options:
ecryptfs_unlink_sigs
ecryptfs_key_bytes=16
ecryptfs_cipher=aes
ecryptfs_sig=bd28c38da9fc938b
WARNING: Based on the contents of [/root/.ecryptfs/sig-cache.txt],
it looks like you have never mounted with this key
before. This could mean that you have typed your
passphrase wrong.
Would you like to proceed with the mount (yes/no)? : <-- yes
Would you like to append sig [bd28c38da9fc938b] to
[/root/.ecryptfs/sig-cache.txt]
in order to avoid this warning in the future (yes/no)? : <-- yes
Successfully appended new sig to user sig cache file
Mounted eCryptfs
root@server1:/home/administrator#
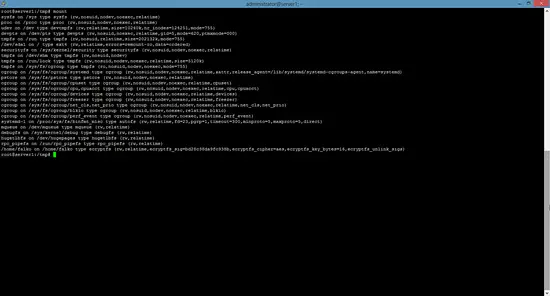
Take a look at the output of
mount
and you should see that /home/falko/ is now encrypted:
Let's restore our backup to the now encrypted directory /home/falko/ and delete the backup afterwards:
cp -pfr /tmp/falko/ /home/
rm -fr /tmp/falko/
For testing purposes, let's copy some other file, e.g. /etc/hosts, to /home/falko/ to check if it really gets encrypted:
cp /etc/hosts /home/falko
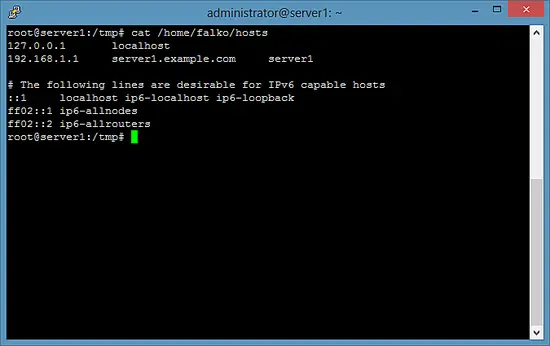
While /home/falko/ is mounted with the ecryptfs file system type, it should be possible to read the contents of /home/falko/hosts:
cat /home/falko/hosts
Now unmount /home/falko/...
umount /home/falko
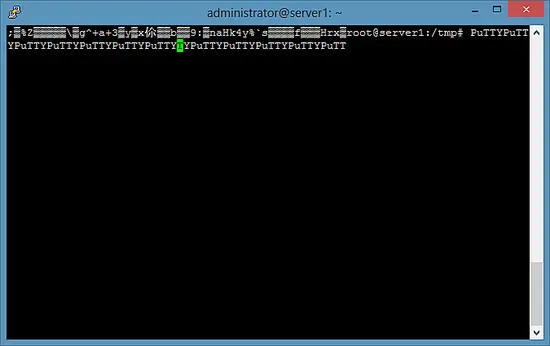
... and try again to read /home/falko/hosts, and you should get some cryptic stuff:
cat /home/falko/hosts
4 How to automatically mount an encrypted partition at boot time
Of course, we don't want to mount /home/falko/ manually each time - it would be nicer if could be mounted automatically at boot time. To do this, we need a passphrase file, and for security reasons I want this passphrase file to be located on a USB key.
Plug in a USB key and run
fdisk -l
to find out its device name and file system type:
root@server1:~# fdisk -l
Disk /dev/sda: 32.2 GB, 32212254720 bytes
255 heads, 63 sectors/track, 3916 cylinders
Units = cylinders of 16065 * 512 = 8225280 bytes
Sector size (logical/physical): 512 bytes / 512 bytes
I/O size (minimum/optimal): 512 bytes / 512 bytes
Disk identifier: 0x00035e35
Device Boot Start End Blocks Id System
/dev/sda1 * 1 3793 30461952 83 Linux
/dev/sda2 3793 3917 992257 5 Extended
/dev/sda5 3793 3917 992256 82 Linux swap / Solaris
Disk /dev/sdb: 8086 MB, 8086617600 bytes
255 heads, 63 sectors/track, 983 cylinders
Units = cylinders of 16065 * 512 = 8225280 bytes
Sector size (logical/physical): 512 bytes / 512 bytes
I/O size (minimum/optimal): 512 bytes / 512 bytes
Disk identifier: 0x000e439f
Device Boot Start End Blocks Id System
/dev/sdb1 1 983 7895916 b W95 FAT32
root@server1:~#
In my case, the device name is /dev/sdb1, and it uses an FAT32 file system.
Let's mount the USB key to /mnt/usb:
mkdir /mnt/usb
mount /dev/sdb1 /mnt/usb
Take a look at the output of
mount
... and you should see that it got mounted with the file system type vfat (FAT32) - we will need this information later on for our /etc/fstab file:
root@server1:~# mount
sysfs on /sys type sysfs (rw,nosuid,nodev,noexec,relatime)
proc on /proc type proc (rw,nosuid,nodev,noexec,relatime)
udev on /dev type devtmpfs (rw,relatime,size=10240k,nr_inodes=124251,mode=755)
devpts on /dev/pts type devpts (rw,nosuid,noexec,relatime,gid=5,mode=620,ptmxmode=000)
tmpfs on /run type tmpfs (rw,nosuid,relatime,size=202132k,mode=755)
/dev/sda1 on / type ext4 (rw,relatime,errors=remount-ro,data=ordered)
securityfs on /sys/kernel/security type securityfs (rw,nosuid,nodev,noexec,relatime)
tmpfs on /dev/shm type tmpfs (rw,nosuid,nodev)
tmpfs on /run/lock type tmpfs (rw,nosuid,nodev,noexec,relatime,size=5120k)
tmpfs on /sys/fs/cgroup type tmpfs (ro,nosuid,nodev,noexec,mode=755)
cgroup on /sys/fs/cgroup/systemd type cgroup (rw,nosuid,nodev,noexec,relatime,xattr,release_agent=/lib/systemd/systemd-cgroups-agent,name=systemd)
pstore on /sys/fs/pstore type pstore (rw,nosuid,nodev,noexec,relatime)
cgroup on /sys/fs/cgroup/cpuset type cgroup (rw,nosuid,nodev,noexec,relatime,cpuset)
cgroup on /sys/fs/cgroup/cpu,cpuacct type cgroup (rw,nosuid,nodev,noexec,relatime,cpu,cpuacct)
cgroup on /sys/fs/cgroup/devices type cgroup (rw,nosuid,nodev,noexec,relatime,devices)
cgroup on /sys/fs/cgroup/freezer type cgroup (rw,nosuid,nodev,noexec,relatime,freezer)
cgroup on /sys/fs/cgroup/net_cls,net_prio type cgroup (rw,nosuid,nodev,noexec,relatime,net_cls,net_prio)
cgroup on /sys/fs/cgroup/blkio type cgroup (rw,nosuid,nodev,noexec,relatime,blkio)
cgroup on /sys/fs/cgroup/perf_event type cgroup (rw,nosuid,nodev,noexec,relatime,perf_event)
systemd-1 on /proc/sys/fs/binfmt_misc type autofs (rw,relatime,fd=23,pgrp=1,timeout=300,minproto=5,maxproto=5,direct)
mqueue on /dev/mqueue type mqueue (rw,relatime)
debugfs on /sys/kernel/debug type debugfs (rw,relatime)
hugetlbfs on /dev/hugepages type hugetlbfs (rw,relatime)
rpc_pipefs on /run/rpc_pipefs type rpc_pipefs (rw,relatime)
/dev/sdb1 on /mnt/usb type vfat (rw)
root@server1:~#
Now take a look at the contents of /root/.ecryptfs/sig-cache.txt:
cat /root/.ecryptfs/sig-cache.txt
bd28c38da9fc938b
We need this signature for the file /root/.ecryptfsrc which we create as follows:
nano /root/.ecryptfsrc
Please make sure that you use the signature from the /root/.ecryptfs/sig-cache.txt file in the ecryptfs_sig line:
key=passphrase:passphrase_passwd_file=/mnt/usb/passwd_file.txt ecryptfs_sig=bd28c38da9fc938b ecryptfs_cipher=aes ecryptfs_key_bytes=16 ecryptfs_passthrough=n ecryptfs_enable_filename_crypto=n
Now we create the passphrase file on our USB key:
nano /mnt/usb/passwd_file.txt
passphrase_passwd=some_passphrase
Make sure that you use the correct passphrase, i.e., the passphrase that you would use if you mounted the directory manually.
Next open /etc/fstab...
nano /etc/fstab
... and add the following two lines (make sure you use the correct file system type for your USB key - vfat in my case):
[...] /dev/sdb1 /mnt/usb vfat ro 0 0 /home/falko /home/falko ecryptfs defaults 0 0
(It is important the the line for the USB key comes before the line for the encrypted partition because the USB key needs to be mounted before the encrypted partition can be mounted!)
Then reboot the system:
reboot
If everything goes fine, your encrypted partition should automatically be mounted after the reboot. However, it is possible that your system cannot mount your USB key during boot, which means your encrypted partition cannot be mounted either. If this happens, edit /etc/rc.local (this script is executed at the end of the boot process)...
nano /etc/rc.local
... and add the line /bin/mount -a before the exit 0 line:
#!/bin/sh -e # # rc.local # # This script is executed at the end of each multiuser runlevel. # Make sure that the script will "exit 0" on success or any other # value on error. # # In order to enable or disable this script just change the execution # bits. # # By default this script does nothing. /bin/mount -a exit 0
This will (re-)mount all partitions (including your USB key and the encrypted partition) at the end of the boot process.
5 Links
- eCryptfs: https://launchpad.net/ecryptfs
- Debian: http://www.debian.org/