Welcome back to the GPG series, where we explore how to make use of GPG with other applications to secure and protect your data. In the first installment, we covered the functions of GPG. You learned about integrity, non-repudiation and authenticity. In the second installment, key creation and publication were covered, as well as revocation certificate creation. This installment will cover using your key to sign and encrypt files or communications.
Key use scenarios
When you use your key, you can sign, encrypt, or both sign and encrypt. Authenticity is guaranteed by using a signature. Privacy is maintained by using encryption. The following scenarios will help illustrate how to use those functions.
Scenario 1 (Authenticity)
I want people to know a file or message came from me. ---- Sign the file or message with your private key.
Scenario 2 (Privacy)
I want to send a file or message only my intended recipient can view. ---- Encrypt the file or message with the recipients public key.
Scenario 3 (Authenticity and Privacy)
I want to send a message that only my intended recipient can read and I want the recipient to be able to verify it came from me. ---- Encrypt the file or message with the recipients public key and sign the file or message with your private key.
Scenario 4 (Authenticity)
I want to verify the identity of a person who apparently sent a file or message ---- Verify the signature using the sender's public key.
Scenario 5 (Privacy)
I want someone to send me a message or file only I can view. ---- Have the sender encrypt the file or message with your public key.
Scenario 6 (Authenticity and Privacy)
I want someone to send me a message or file only I can view and I want to be able to verify the identity of the person who apparently sent the file or message. ---- Have the sender encrypt the file or message with your public key and sign it with their private key. the
In the first part of this series, it was noted that GPG makes use of asymmetric cryptography. A public key can be used to encrypt a file or message that requires the paired private key to decrypt it. If you were to encrypt a message with your private key, anyone with your public key could decrypt it. This is why the public keys are used to perform the encryption in the scenarios listed above.
Using a GPG key with Evolution
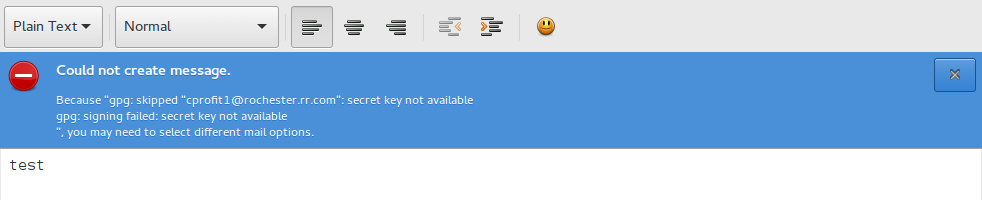
When you send a message using Evolution, you have the option to sign a message, encrypt a message, or both sign and encrypt a message. Once you have created a key as described in GPG key management, part 1, it can be used in Evolution in an individual message or set as a default for specific accounts. First, you have to make the key available to the account(s). If you fail to do this, you will get an error message if you attempt to sign or encrypt your email.
To select a key for an account, you select Edit > Preferences from the Evolution menu.
You then select the account you want to use your GPG key with and click the Edit button.
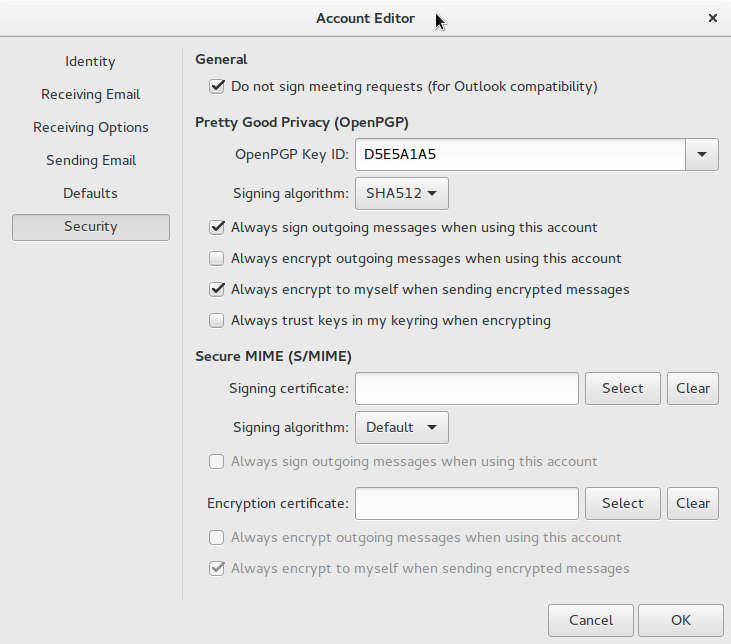
That will bring up the Account Editor and you will be able to select a key. Then you can choose other default options for signatures and encryption for that account under the Security section.
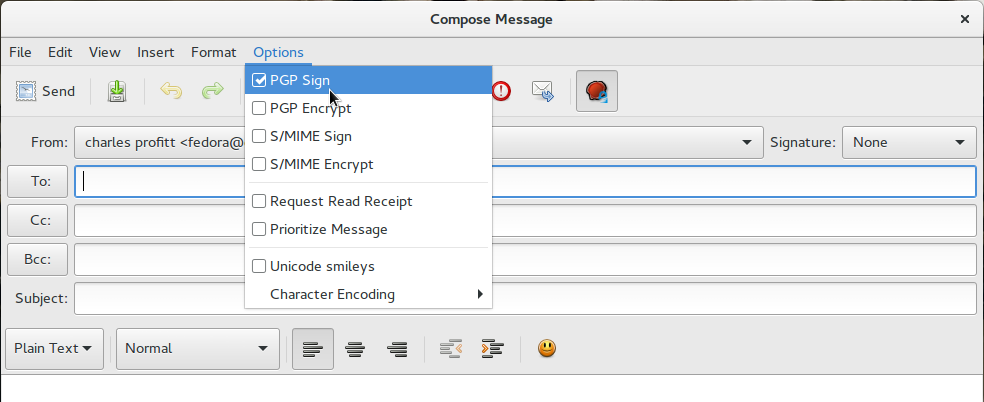
The options selected above are good defaults for authenticity. You can override these selections for each email on an individual basis, so choose the options you will use most often. I will caution against trusting keys automatically. The reason for that will be covered in the fourth installment of this series when the Web of Trust is covered in greater detail. It should be noted that each account must be configured individually.
The example above shows how to override the default settings for the account when sending an email. Simply select Options and then check the appropriate boxes. Note that if you have not chosen a key for use with the account, you will get the error message described above.
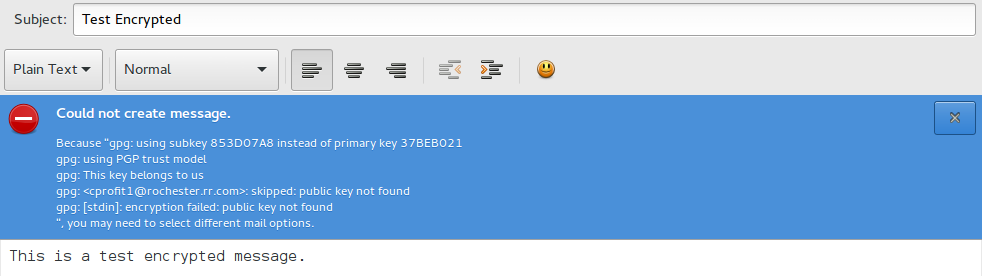
If you choose to encrypt a message, you will need to have downloaded the recipients public key. If you attempt to encrypt a message without it, you will get an error message like the one below.
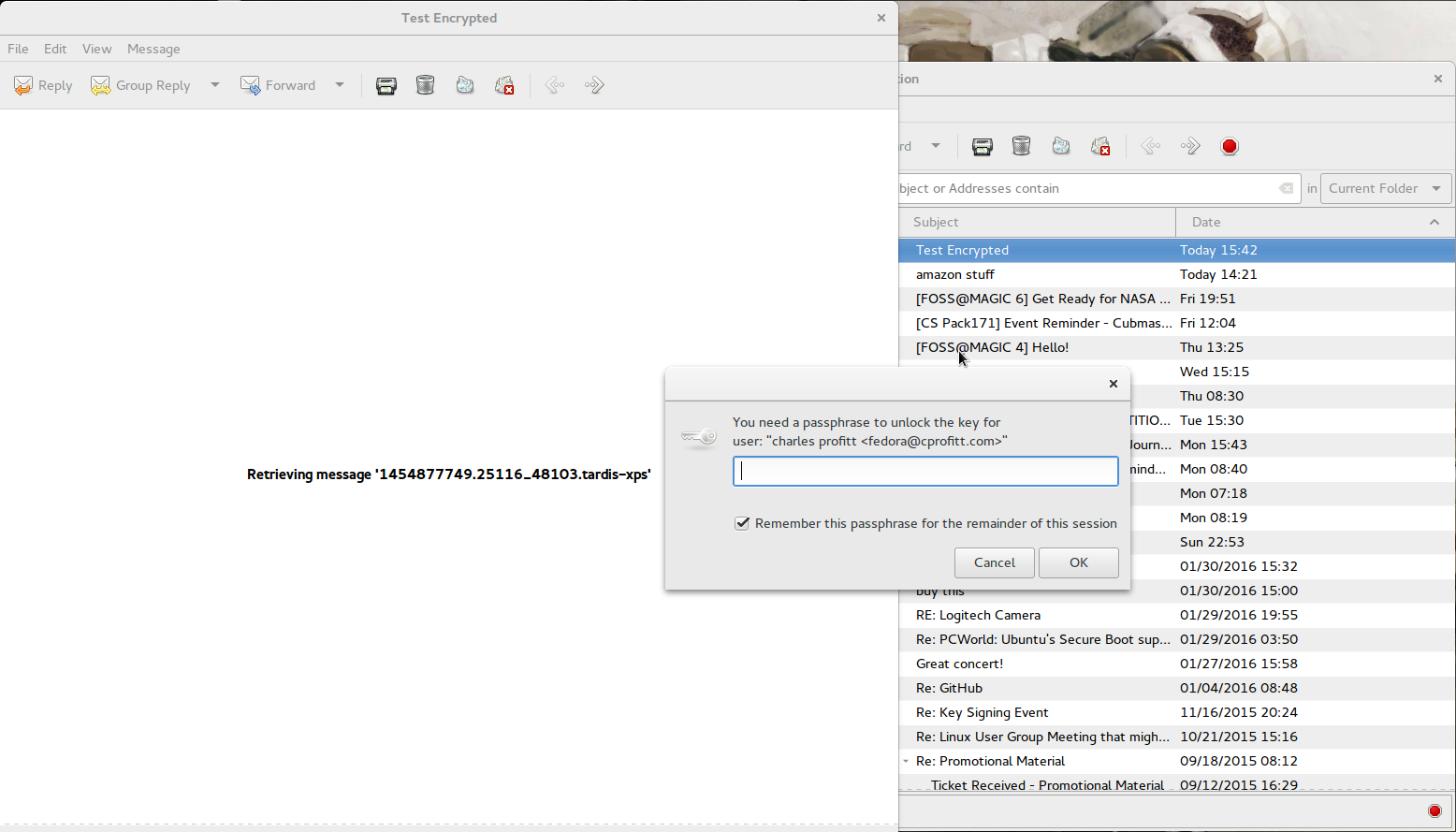
When you receive an encrypted email, depending on how they were sent, you will be able to decrypt the mssage directly in Evolution. When you open these messages you will be prompted to use the passphrase for your key.
After entering your passphrase successfully, the message will be shown in the Evolution email window.
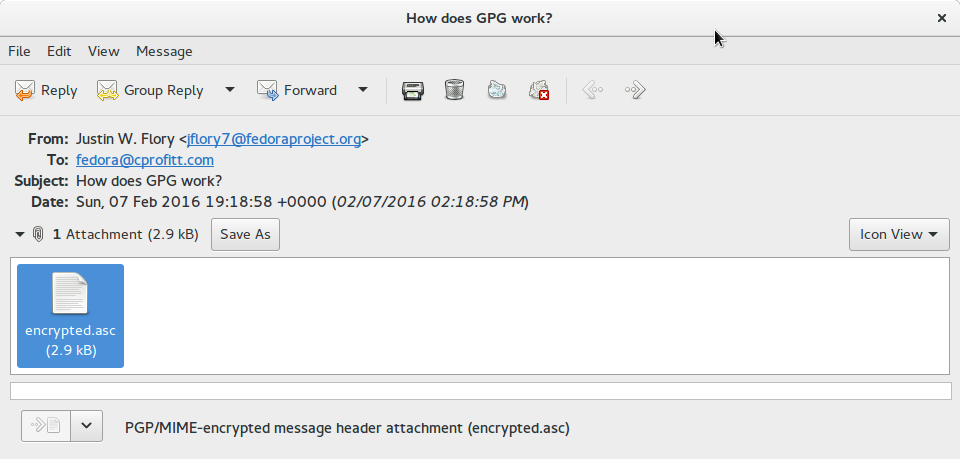
There are other times when encrypted messages will appear as attachments and you will not be prompted to decrypt them in Evolution.
For these messages, you have to save the attachment and decrypt the message using the command line. The message contents will be similar to the text below.
-----BEGIN PGP MESSAGE----- Version: GnuPG v2 hQIMAyuJQ2CFPQeoAQ/+M6WWOl3hjSl0/ugFVHHPBw7jd7Ib/DgoVoQ0Loy+W24D c7xU9bmtFeRpWs2sFUllwdTfaq8PmQ/dKfFJjKu+u9QhMoWKLw48SQu10M+7M2zs B77sImYVIOHrXaB6wLNpC0eM6hnjEhwqyEzCxFqpCWByPr+v4e+GAfm96SoStJ2F kRf8XSm5n1IMgU02YSSjNiVE2ObbcbC+xNPu3E7rbfdp7jfpOoX6+U1+XtaSEIll 4l2+Fza3VhdEAzg25TK2ua3RVxUkok37WVVpQj2R4F21egUaUu4Mq3cdw5Cq54bf 5yFDFhmuEWNgaxolhcrcZAbIK6JjHnlwiiLfAVBkepBE+iltUzknwcnKqysxl/Z7 TiE22CLK8+80Haw1BvB/nBvj87XGqb2F0i+qiN9JLToSd5/fy4cCXdbWlnGRlvWg cVfnyOpp1/nGvmgB/1KN1gq47DUjEUK3M9dzbp8h6q9rpHGlo3e2BQcY0IRGeZEq 2eTYxYlFhbvEbQ+RS0+ktZKEBlVGltffWbzHakoeP5I7lhTaw1Ld1kNlYcNqdqdU JLn9Q9N/aaei3/HeV9FLdRrD2mZE1xhA9f9TzXQcb5KVhnz2EPg0yjaHuxvGNaZX YNXVzxAtaoJ+PbaqgtvxAADNBtORuu9XiMe+72CgkxMMcCl1FESXri/lCkTvf8KF AgwD5iRJs1CGK9kBD/4pLQ7wVWiSU9YbsmOJ3pbbD/qumR5nCbHvbqvTx0HvU1zE wUJ/7gK9UG6YUpJJWDx/XvbVN1b/s53ZPRp6FdGxQ5nrktKU1TXVwlzbwGxvZyCD HkiqRJJWFnI6o8m71jB8tBo5xdMNznckxX/dy6iPzQzvUkq9MbUoEWgLDS9FgQHH Gf8XQr7fqRKu391UrArtLz1LHr1YDtF5ALVczE2DnwaMdEdMWzly+Pqzc0cF3ptR xRsmIwuiNYZ/bopux12HVXzvOzLbkEVcrjUSoyKzTlmJ1Ms0UA7U/opgyzA6tEyl oFNIRjDi2zfX4rWDlvd3+jnGZhwVPkqd7r9V9CmwVv501Z5jzGmbCqYJ1jdEJ24m 9LE7sG5X0GoH3jzx9i1f1/NTCKUu44jVMDxeeeyVrzsJRe4Qktt0lXm/KW+TpueZ izSyb82p4ruYcTktVNhbYNZLafeddHYu+g+HcPD/cZCkPMamN9AM2+UjnOZzVO6P jZIYN1K938b5dUZO7JBtgo2m/MSzXyjwwKAP3mUq+BUn0EdhNp7strGE/31TbhPO nwxzZegEQyQRHbaD28RmjamYJp6iEs/uov4GKsD74XlgmuRE8PGM9mVWte8H4r4a 3luMuSdbrzYlIVsurmUIhbZdoRow2ZRgS1Ns2nYxt7cOfhefnYeBtP5tpmT6XtLp AWj5lYYgC4oKsAC6l4ZNTijszIypwTkKFK8cI9yviEx4zoU4Nbd1xVs67WJmAemR GHpZBBw4ldFNktf1xPvpIFd4C/KWYVBIexpiHwDxaTcGh+nfxlNbehqhbSEZc/TT 033eRFmZ/7HA+3aHZiTkbQa789H2ZxAqkr2RgZkJp2BxtPkUiK4B35zr3h1XGaQ9 3+WIVTKUu7hqkR6ncngPZBWkdaQEuI+CHvqIzuosWasX1OzLbMNxr8V+HjTA8P1o XaGKzo74Eu9i4luE5TBpUiQgCtxhH+Jr5F88dJoWZvWJVJ4Ih1brKcLi9dsbtsT2 vxEq4dA9YyyXS6ks6xBUz7OqCAz0Hi3H0xJP3HkPnnGuAvY1JhrkrojNXpnIuuKS 3heFQEy60QYqCEFqfCLl8AotVETuKUqFVQMRn/6wxXKCzou3Kh8AYHAuQ4pIggJO l7M28cgBQLPI+m9EXATSYHe9ZXh4+poceIUfTQIRXeXLBbtoOdB5laC439CuZXkP pZQMoQA8/6TaQm8r5Ubkd+l19tyfjtzaKapvDaYL3XCnHRVtRmfD5SAIUBx/iGvt OBOkzMtEqIiHATczWYOsHKzj9s+wx/D6f6AIa2iDwar8R/yxFsDHNhCwGLbWeoml FQpb1Lnowar/Csz0ujOeCr/vhywI+UkNcAbcuAq/LrjBMpavf22OX6kA0D7EGQ1O JJwmg+xI+3hq1aATLYwc0UElLdnicufM4cJEKkX1nqFw3ytYxRJn+JlqKvE7qvVp RG1YGS14yf6GcRl558h2BI8zNsNussEfwTLvSPSWlqUgGEnjlIKI9oiVNQacmIJm DGfcPqNzTc28sTYJl4Yuz7J5dPwe3FBy3+kWwbaCCjaP5IyES1MVLpoF1l/qQRLs QN6GjUaDVd17plH6g2lYX91SrSwFF/SnkptJ1vBcqLKvoT7XVWUucF86tny0+/3u dHRmOCjwyxOFjYp2D/ooCGCqQC4USJm3f1HDCw/niv+7CY1wvXJcrPQqs7ZHLNA3 PTqUSGW7+zru8K0zYdLdt3gGw1PJahxdw8c2E3z/lO8O9TvwdMwvlEf5CaTniT+3 JBb1NrIFZcueLcR2r3DzcoDON4Lx/vz+sBdJO5v3YI6JzKvgZbz3tD/4qJ7v3IMK lpt53HgGtPpQwKNLFXNtllsIbatKI4BBPUtZhj1ixwJ9o5snBlvAOAKVVXHaOi4E Kz5DYuHtr1mc9Ev4gxBajTHIvUGhOUEt5VYNPXnujvHDMkjoTeZk6myoSS61387A oe2/2SQ2URTizpXxuiZno3P5CtiH81OrXUSQg2g+n00s/DUdPdkQkiLI6PmXdbi+ JUOxrg== =n6A0 -----END PGP MESSAGE-----
Decrypting the saved text files will be covered a little bit later in this article.
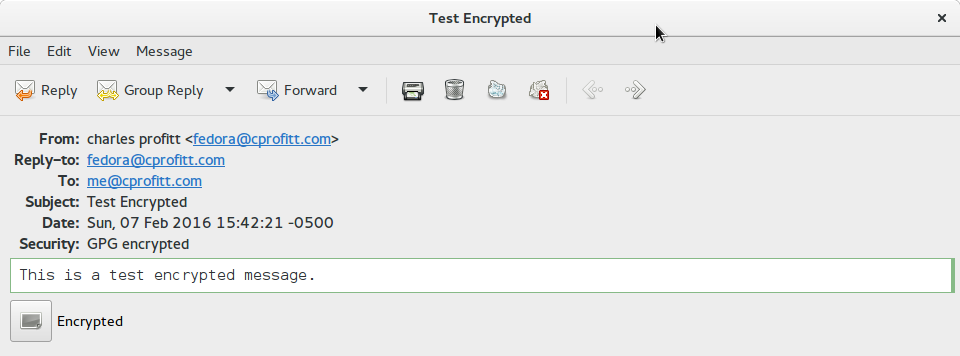
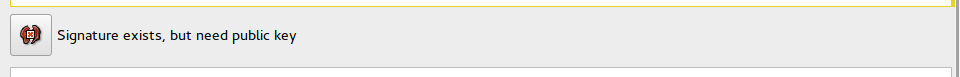
Evolution automatically verifies signatures at the bottom of every email. There will be an area similar to the ones below.
Encrypting and decrypting files
In addition to sending and receiving encrypted emails, you can encrypt and decrypt files with GPG. While one usually thinks of using encryption for sending information securely to someone else, it can also be used to keep information secure while still in your possession. For example, you could keep a list of passwords in an encrypted file. This would prevent information from being compromised if your laptop was stolen.
Example: Encrypt a file names plain.txt
$ gpg2 --encrypt -r fedora@cprofitt.nrl plain.txt
If you do not specify the recipient with the
option, you will be prompted to provide one.
$ gpg2 --encrypt plain.txt You did not specify a user ID. (you may use "-r") Current recipients: Enter the user ID. End with an empty line: fedora@cprofitt.nrl
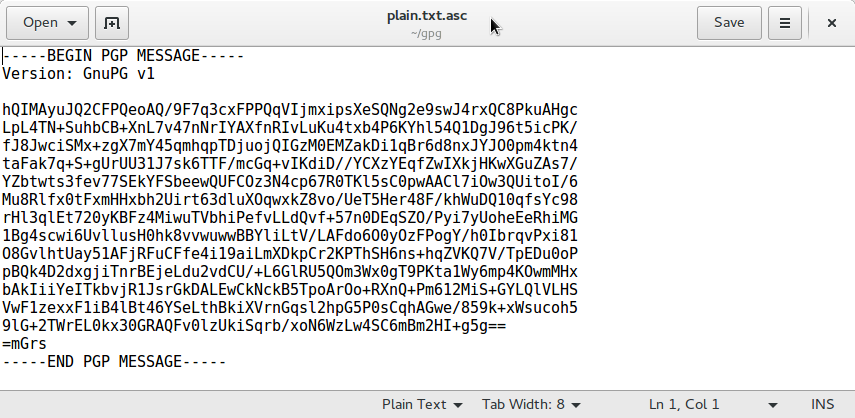
Remember that you need the recipient’s public key in order to encrypt the file. The recipient will decrypt the file with their private key. This style of encryption produces a binary file. If you would prefer to produce a text file, you can use an option to ASCII Armor the file.
$ gpg2 --encrypt --armor -r fedora@cprofitt.nrl plain.txt
If
is not specified, the resulting file will be
. If
is used, the file will be
. The resulting .asc file can be opened and the ASCII text can be copied and pasted in to another application. This could be useful if your email application does not support GPG and you want to send an encrypted message.
It should be noted that when you encrypt a file using another person’s public key, you will not be able to decrypt the file yourself. If you want to encrypt a file for yourself, you could specify yourself as the recipient or use the
option. This will use only a passphrase to encrypt the file.
$ gpg2 --symmetric plain.txt Enter passphrase: Repeat passphrase:
You can also choose to use the
option if you wanted to create an ASCII file.
$ gpg2 --symmetric --armor plain.txt Enter passphrase: Repeat passphrase:
Decrypting files is much easier because it does not matter if the file is binary or ASCII, or if it was asymmetric or symmetric. With plain text, you have an option to direct the output to a file or to the terminal (stdout).
To send the output to stdout, you can run the following command.
$ gpg2 -o - plain.txt.gpg You need a passphrase to unlock the secret key for user: "charles profitt <fedora@cprofitt.nrl>" 4096-bit RSA key, ID 853D07A8, created 2015-11-15 (main key ID 37BEB021) Enter passphrase: gpg: encrypted with 4096-bit RSA key, ID 853D07A8, created 2015-11-15 "charles profitt <fedora@cprofitt.nrl>" This is secret text
To send the output to a file you can specify the file by using the
option or have it use the default which will create a file without the .gpg or .asc extension.
$ gpg2 plain.txt.gpg You need a passphrase to unlock the secret key for user: "charles profitt <fedora@cprofitt.nrl>" 4096-bit RSA key, ID 853D07A8, created 2015-11-15 (main key ID 37BEB021) Enter passphrase: gpg: encrypted with 4096-bit RSA key, ID 853D07A8, created 2015-11-15 "charles profitt <fedora@cprofitt.nrl>"
If you want to specify a file output name, you can run the command the following way.
$ gpg2 -o plain.2.txt plain.txt.asc You need a passphrase to unlock the secret key for user: "charles profitt <fedora@cprofitt.nrl>" 4096-bit RSA key, ID 853D07A8, created 2015-11-15 (main key ID 37BEB021) Enter passphrase: gpg: encrypted with 4096-bit RSA key, ID 853D07A8, created 2015-11-15 "charles profitt <fedora@cprofitt.nrl>"
Signing files
Signing files is similar to encrypting them, but by default the signature will use your private key. The recipient of a file will use your public key to verify the signature. By default, the resulting file will be a binary file. If you use the
option, it will produce an ASCII file with the .asc extension.
To sign a file with GPG, run the following command.
$ gpg2 --sign plain.txt You need a passphrase to unlock the secret key for user: "charles profitt <fedora@cprofitt.nrl>" 4096-bit RSA key, ID 37BEB021, created 2015-11-15 Enter passphrase:
You can also sign it using ASCII.
$ gpg2 --armor --sign plain.txt You need a passphrase to unlock the secret key for user: "charles profitt <fedora@cprofitt.nrl>" 4096-bit RSA key, ID 37BEB021, created 2015-11-15 Enter passphrase:
Remember that despite the fact that both of the files have been encrypted, anyone with your public key will be able to decrypt them and verify the signature.
Alternative ways to sign
There are two other options for signing files. If you want to leave the original contents unencrypted, you can use either
or
. The
option will add a signature in ASCII directly to the file. The
option will only work as expected with plain text documents. If you want to leave a graphic or LibreOffice documents unencrypted but signed, you should use the
option. This will create an additional file as a detached signature to be sent with the file.
You can use the
flag as follows.
$ gpg2 --clearsign plain.txt You need a passphrase to unlock the secret key for user: "charles profitt <fedora@cprofitt.nrl>" 4096-bit RSA key, ID 37BEB021, created 2015-11-15 Enter passphrase:
The resulting file can be opened and read with an ASCII signature added to the file.
To use the
option, run this command.
$ gpg2 --detach-sign test.odt You need a passphrase to unlock the secret key for user: "charles profitt <fedora@cprofitt.nrl>" 4096-bit RSA key, ID 37BEB021, created 2015-11-15 Enter passphrase:
This results in the original file being unmodified and an additional file named test.odt.sig that can then be verified using the following command.
$ gpg2 test.odt.sig gpg: assuming signed data in `test.odt' gpg: Signature made Sun 07 Feb 2016 10:37:49 PM EST using RSA key ID 37BEB021 gpg: Good signature from "charles profitt <fedora@cprofitt.nrl>"
The signature can only be verified if the original file is available to the user. If the original file is in the same directory it will be used automatically. If the file is not then the you will be prompted to provide the path to the original file.
Regardless of the type of signature used, if the file was modified, GPG will report a bad signature.
$ gpg2 test.odt.sig gpg: assuming signed data in `test.odt' gpg: Signature made Sun 07 Feb 2016 10:37:49 PM EST using RSA key ID 37BEB021 gpg: BAD signature from "charles profitt <fedora@cprofitt.nrl>"
You can also encrypt and sign a file at the same time by combining the commands as follows:
$ gpg2 --armor --recipient fedora@cprofitt.nrl --encrypt --sign plain.txt You need a passphrase to unlock the secret key for user: "charles profitt <fedora@cprofitt.nrl>" 4096-bit RSA key, ID 37BEB021, created 2015-11-15 Enter passphrase:
When you decrypt the resulting file, you will get additional output verifying the signature was good or bad.
$ gpg2 plain.txt.asc You need a passphrase to unlock the secret key for user: "charles profitt <fedora@cprofitt.nrl>" 4096-bit RSA key, ID 853D07A8, created 2015-11-15 (main key ID 37BEB021) gpg: encrypted with 4096-bit RSA key, ID 853D07A8, created 2015-11-15 "charles profitt <fedora@cprofitt.nrl>" gpg: Signature made Sun 07 Feb 2016 11:12:26 PM EST using RSA key ID 37BEB021 gpg: Good signature from "charles profitt <fedora@cprofitt.nrl>"









David Liteman
Excellent tutorial. I learned a lot about gpg. Is this the last installment?
Schwella
No, it was written that there will be a fourth installment about the web of trust 😉
Hopefully there is a description of how to get the public keys of persons, I want to trust, in an easy way.
Charles Profitt
Yes, the fourth installment will cover getting public keys, signing public keys, the web of trust and a few other topics on managing keys.
Pranavk
Are we also going to discuss about subkeys ? I found those very useful when one want to encrypt/sign from multiple devices without having the fear of loosing your private key to someone else. Because ideally, you only need your private key when you want to sign someone else’s key. For common tasks such as encrypting and signing a message, you can do with subkeys.
Charles Profitt
I planned on covering them, but not in great depth.
David Liteman
Isn’t the command required to verify a signature in gpg? I noticed up above on the verify signature section, it is not used. When I type in the command as you have it, gpg announces that file already exists and asks to overwrite. Please advise.
David Liteman
part of my message up above was omitted. What I meant to ask is, Isn’t the –verify command necessary to verify a signature in pgp? in your example up above I don’t see it, and when I enter the command as you have it, pgp announces that the file already exists, and asks me if i want to overwrite? Pleas advise.
Charles Profitt
Yes, just use gpg –verify if you want to verify the signature. In the example I gave you are decrypting and verifying in the same step.